
Network Vulnerability Assessment
Uncover hidden risks in your network and unlock critical insights with a forensics-driven approach.

Enhance your network security using a risk-based approach to vulnerability assessment
SISA’s vulnerability assessment services combine automated and manual scans to offer 360° view of potential threats within your network.
Non-intrusive PCI-approved ASV scan
Our PCI-approved ASV scan ensures a thorough assessment of your network’s security without disrupting its normal operations.
Component-level root cause analysis
Our experts perform a meticulous analysis to identify the underlying causes of vulnerabilities within your network infrastructure.
Network and system architecture review
We conduct a detailed examination of your network and system architecture, identifying any weaknesses or vulnerabilities that may exist.
Redundancy evaluation in entire infrastructure
We assess the redundancy measures in your infrastructure to enhance resilience and ensure business continuity.


Uncover, assess and analyze network vulnerabilities to protect against evolving threats
Our expert network security team helps you uncover vulnerabilities and preemptively counter the risk of expensive data breaches.
Key benefits of network vulnerability assessment
- Identify security flaws across the entire network infrastructure before hackers target them.
- Stay on top of compliance obligations and achieve security certifications with ease.
- Foster customer trust, safeguard your business reputation and gain a competitive advantage.
- Proactively mitigate security risks and stay ahead of cyberattacks.
Leverage SISA’s vulnerability assessment services to develop a robust network security strategy
SISA’s vulnerability assessment uses a five-phased approach to identify the flaws and reduce the blind spots in your network.
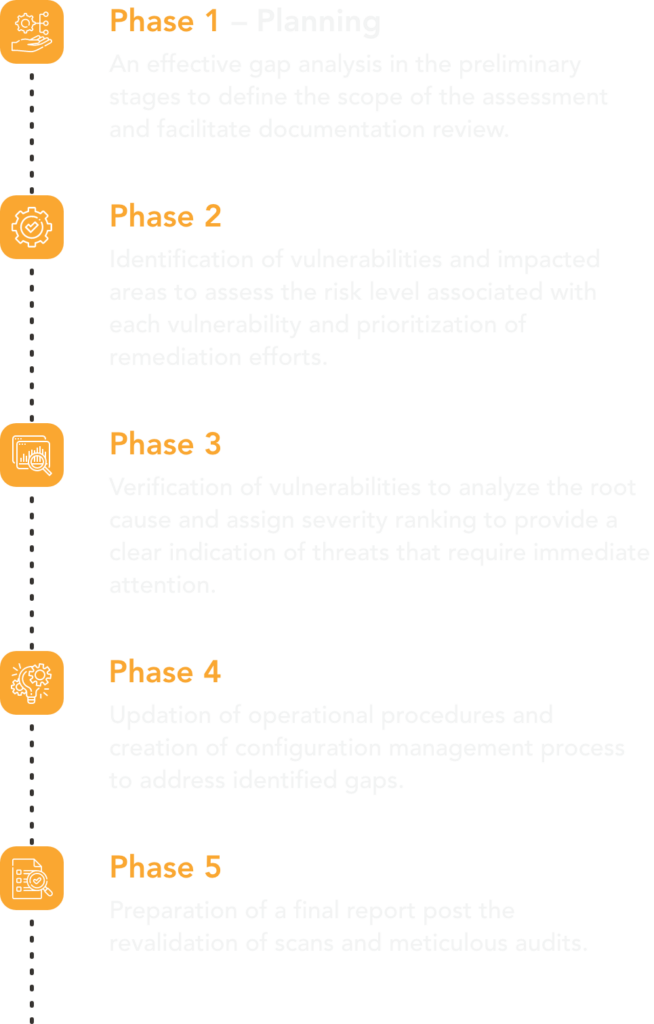
Phase 3 – Analysis & Reporting
Verification of vulnerabilities to analyze the root cause and assign severity ranking to provide a clear indication of threats that require immediate attention.
Phase 2 – Execution
Identification of vulnerabilities and impacted areas to assess the risk level associated with each vulnerability and prioritization of remediation efforts.
Phase 1 – Planning
An effective gap analysis in the preliminary stages to define the scope of the assessment and facilitate documentation review.
Phase 4 – Remediation
Updation of operational procedures and creation of configuration management process to address identified gaps.
Phase 5 – Revalidation & Reporting
Preparation of a final report post the revalidation of scans and meticulous audits.
Why choose SISA for network vulnerability assessment?
SISA’s vulnerability assessment combines human expertise, advanced technology and robust methodology to offer swift, secure, and reliable service.
PCI SSC authorized Approved Scanning Vendor (ASV)
CREST-accredited framework
Integration of forensic-driven learnings into testing techniques
A robust use case library with 10+ years of experience for broader threat coverage.
A specialized non-intrusive ASV solution for a systematic and exhaustive assessment.
Featured Insights
Request a Call

SISA is a global forensics-driven cybersecurity solutions company, trusted by leading organizations for securing their businesses with robust preventive, detective, and corrective cybersecurity solutions. Our problem-first, human-centric approach helps businesses strengthen their cybersecurity posture.
Industry recognition by CREST, CERT-In and PCI SSC serves as a testament to our skill, knowledge, and competence.
We apply the power of forensic intelligence and advanced technology to offer true security to 2,000+ customers in 40+ countries.
Company
Resources
Quick Links
Copyright © 2025 SISA. All Rights Reserved.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global


 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube







