Why to integrate PCI DSS and HIPAA?

“Compliance” is a big word for IT industry which is driving a significant amount of business. While following different rules, regulations and standards, you are not just avoiding potential fines and penalties but you are also gaining huge customer trust by ensuring their data is safe and secure in your custody.
PCI DSS and HIPAA are some of the largely applicable and followed standards from the plethora of information security standards. Comparatively, HIPAA is vague a standard than PCI which is somewhat more straight forward. But their focus is on completely two different kinds of data. For PCI, the “crown jewel” of data is the payment card information while for HIPAA it’s the individual’s health information wherein privacy is the main concern.
Both PCI DSS and HIPAA lays down penalty conditions in case of breach of data but it should be noted that HIPAA is a U.S government regulation while PCI is dictated by the Security Standards Council formed by five major payment brands. There are many common controls, which are later explained in this article that overlap these two standards and this should be looked upon as an advantage for organizations looking for complying both. From the cost perspective as well as execution of controls wise, it may seem lucrative to hit two birds in one stone!
The rest of this article explains these two standards in brief, their comparison and overlapping requirements and benefits of combining both.
PCI DSS
Payment Card Industry Data Security Standard is one of the most granular and specific standard aiming towards securing credit and debit card related information. It applies to all entities involved in payment card processing – including merchants, processors, acquirers, issuers, and service providers, as well as all other entities that store, process or transmits cardholder data (CHD) and/or sensitive authentication data (SAD). PCI DSS is Industry regulation enforced by payment brands and has set 6 goals, broken into 12 requirements and more than 300 sub-requirements to be implemented within the cardholder data environment.
Build and Maintain a Secure Network and Systems
1. Install and maintain a firewall configuration to protect cardholder data
2. Do not use vendor-supplied defaults for system passwords and other security parameters
Protect Cardholder Data
3. Protect stored cardholder data
4. Encrypt transmission of cardholder data across open, public networks
Maintain a Vulnerability Management Program
5. Protect all systems against malware and regularly update anti-virus software or programs
6. Develop and maintain secure systems and applications
Implement Strong Access Control Measures
7. Restrict access to cardholder data by business need to know
8. Identify and authenticate access to system components
9. Restrict physical access to cardholder data
Regularly Monitor and Test Networks
10. Track and monitor all access to network resources and cardholder data
11. Regularly test security systems and processes
Maintain an Information Security Policy
12. Maintain a policy that addresses information security for all personnel
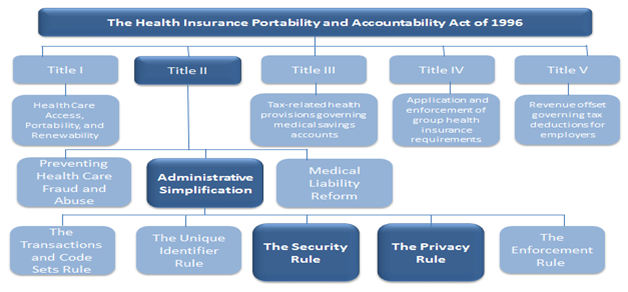
What is HIPAA?
HIPAA stands for ‘Health Insurance Portability and Accountability Act’. It is focused on protection of privacy of individually identifiable health information and gives patients an array of rights with respect to that information. It is applicable on Covered Entities (CE) and Business Associates (BA) which are generating, accessing, processing and transmitting PHI. HIPAA is a legal requirement, governed by the US government.
HIPAA Basics
The Security Rule- It specifies Administrative, Physical and Technical safeguards for Covered Entities (CE) and their Business Associates (BA) to assure Confidentiality, Integrity and Availability of electronic PHI (Protected Health Information)
The Privacy Rule- Privacy Rule provides federal protections for individually identifiable health information held by covered entities and their business associates and gives patients an array of rights with respect to that information. At the same time, the Privacy Rule is balanced so that it permits the disclosure of health information needed for patient care and other important purposes
Challenges
The figure below shows the per capita cost for the consolidated sample by industry classification. Heavily regulated industries such as healthcare, financial, pharmaceuticals, transportation and communications had a per capita data breach cost substantially above the overall mean of $136.
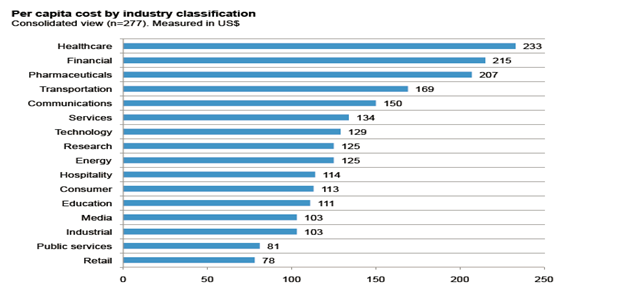
Source: 2013 Cost of Data Breach: Global Analysis- By Ponemon
http://www.ponemon.org/library/2013-cost-of-data-breach-global-analysis
The HIPAA and HITECH Act set forth rules and penalties for healthcare organizations to secure their ePHI and become compliant. While majority of the healthcare practices accept credit and debit cards as payment, they often overlook the protection and security required for cardholder data. Hence it is equally important for organizations to secure ePHI and Cardholder data with utmost importance.
Some Facts
Some significant trends from the ‘2013: Breach report: PHI’ by Redspin that draws our attention to the importance of protecting health information.
| 804 | -Breaches of protected health information since 2009 |
| 29,276,385 | -Patient health records affected by breach since 2009 |
| 7,095,145 | -Patient health records breached in 2013 |
| 137.7% | -Increase in the number of patient records breached in 2012-2013 |
Source: Redspin-2013-Breach-Report-Protected-Health-Information-PHI.
http://www.redspin.com/docs/Redspin-2013-Breach-Report-Protected-Health-Information-PHI.pdf
Healthcare information being more sensitive and valuable is attacker’s most favored. According to the study conducted by Ponemon institute on Patient privacy and data security, it is noted that billing and insurance records and medical files are the most likely to be lost or stolen. The graph below throws more light on the type of patient data lost or stolen.
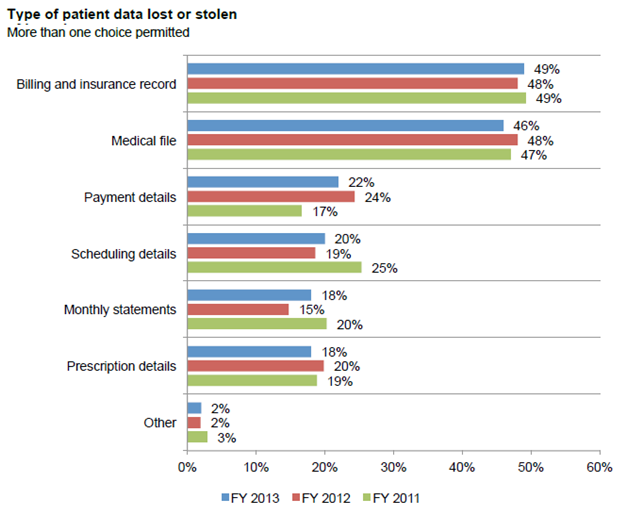
Source: Fourth Annual Benchmark Study on Patient Privacy and Data Security – By Ponemon
Comparison between HIPAA and PCI DSS
| Control | HIPAA | PCI DSS |
| Risk Assessment | Yes | Yes |
| Information System Activity Review | Yes | Yes |
| Access Control and Access Management | Yes | Yes |
| Security Roles and Responsibility | Yes | Yes |
| Workforce Security | Yes | Yes |
| Entry and Exit Process | Yes | Yes |
| Training and Awareness Program | Yes | Yes |
| Protection From Malware | Yes | Yes |
| Log-in monitoring | Yes | Yes |
| Account and Password Management | Yes | Yes |
| Security Incident Response Plan | Yes | Yes |
| Transmission Security | Yes | Yes |
| Contingency Plan | Yes | N/A |
| Evaluation program | Yes | Yes |
| Third Party Security | Yes | Yes |
| Physical Security | Yes | Yes |
| Device and Media Control | Yes | Yes |
| Policies and Procedures and Documentation | Yes | Yes |
| Integrity Protection | Yes | N/A |
| Denial Of Service | Yes | N/A |
| Workstation Security | Yes | Yes |
| Standard Operating procedures | Yes | Yes |
Why to combine PCI DSS and HIPAA?
Combining PCI DSS and HIPAA will help to secure the two most critical types of data i.e. PHI and account data. Hence in one go you can hit 2 birds with the same stone. There are many common controls in between these two standards, which will be reducing significant overhead and repetition if both the standards are implemented simultaneously. Designing the controls in a way such that they cater to the needs of both the standards will surely lessen reengineering effort and redundancy of controls. And all this in return will guarantee lesser audit cost and efforts!
Simple Steps to be followed:
- Initially, identify the system components which are dealing with PHI and account data directly.
- Understand the common infrastructure such as antivirus, log monitors, active directory, etc. supporting both standards requirements.
- Perform Risk Assessment considering PHI and Account Data in scope of assessment
- Ensure Third-party Service provider, Business Associate , Contractor which is compliant to PCI DSS and HIPAA if both type of data is being shared – Example Datacenters
- Deploy common controls as PCI DSS and HIPAA – ‘Required Control’ first
- Follow mitigation step for the Risk identified for PCI DSS and HIPAA- ‘Addressable Controls’
- Deploy specific controls covered in PCI DSS for Account Data and HIPAA for PHI
- Draft / Update Policy and procedure – As per more strict control by PCI DSS or HIPAA. For common domains and cover specific control separately
- Audit and get Compliant for PCI DSS and HIPAA
Conclusion:
Using PCI DSS as a framework will not meet every auditable point on HIPAA compliance checklist. But, it’s a good approach and you will notice during the course of compliance that there are many similarities and meeting those becomes much simpler. Having complied with PCI does not mean that you are HIPAA compliant. Neither the reverse is true. Although they overlap, they remain as two distinct standards and should be treated as such. In order to meet compliance in the right way, OCR audit checklist should be followed for HIPAA and PCI DSS for PCI compliance. In the end, it’s not just about being compliant and flaunting a certificate, but, a more diverse approach with holistic security as an objective will pay in the long run.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  Twitter
Twitter Youtube
Youtube








