PCI DSS – 5 Most Commonly Observed Control Failures

Companies must pay attention to 5 most common control failures, or it will become challenging for them to be compliant to PCI DSS.
Failure to maintain PCI DSS compliance could lead to fines, imposed business restrictions, and rejection of credit card processing facilities. Unfortunately, many companies have not had sufficient time to pressure-test their security controls against all PCI DSS requirements.
Based on our experience of implementing PCI DSS across the globe, these are the common controls of PCI DSS that most companies have failed to achieve.
Requirement 1.1.3.a: Establish a diagram that shows all cardholder data flows across systems and networks
It is of utmost importance for businesses dealing with cardholders’ data to be aware of the locations where the data resides. However, most businesses have failed to do so only because a lot of payments card data remains unmanaged and uncategorized, dispersed across multiple databases of an enterprise.
As truly mentioned by analyst John Kindervag, “This is a breach that should’ve never happened. The fact that three-digit CVV security codes were compromised shows they were being stored”, in the case of the high-profile data breach case of Target, which exposed 40 million credit and debit card data. Storing card data was banned by PCI SSC but wasn’t discovered by Target. As a result, the mishap had to take place.
SISA’s Approach: To meet this PCI DSS compliance control, businesses must map the business systems through which the cardholder data enters the organization and leaves all the way through. To establish a diagram that shows how cardholder data flows across systems and networks, businesses can depict the cardholder data environment, devices and systems with all payment channels, applications and associated protections on CHD based on locations, using a labelling method for identifying the transport mechanism and crucial dependencies.
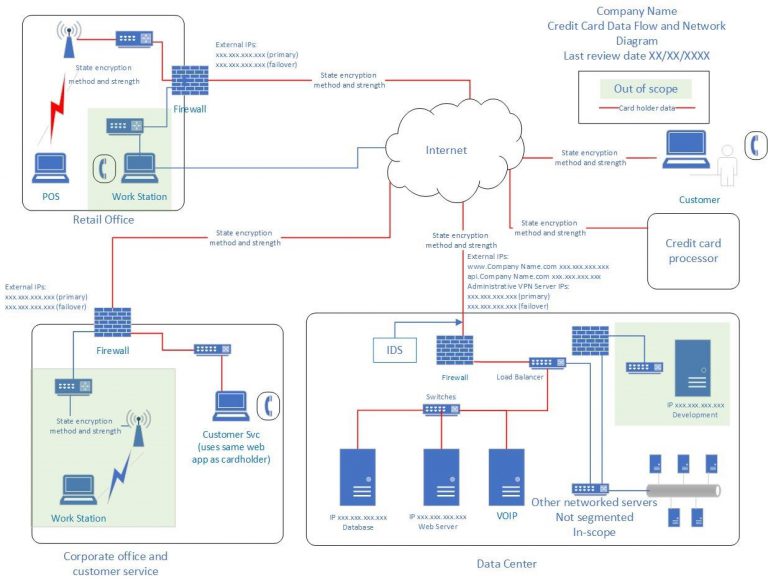
Source: British Standards Institution
Requirement 12.1: Establish, publish, and maintain a security policy
Pretty straightforward – PCI requirement 12.1 states, “Establish, publish, maintain, and disseminate a security policy.”
Many businesses even though have established security policies, they fail to maintain the same that open multiple vulnerabilities in the payments lifecycles. This has been noticed to happen with companies that have documented and published a security policy for the PCI DSS compliance requirement but have not actually used them.
SISA’s Approach: When creating a security policy for the PCI DSS compliance requirements, the organizational design must be brought into work. First and foremost, create a policy to address every requirement of PCI DSS and ensure that it is structured to match the order and language of the PCI DSS sub requirements. Moreover, businesses must review and update at least annually to effectively maintain the security policy.
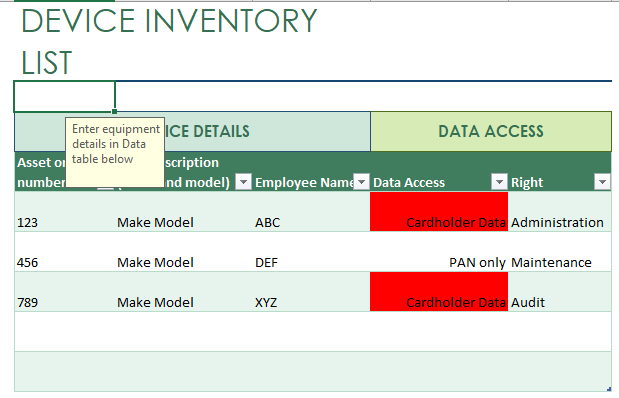
Requirement 12.3.3: List devices and personnel with access to data
Tracking card data is directly proportional to tracking the people that process and store it. However, most of the businesses attempting to comply to PCI DSS compliance requirements fail due to this important control. It happens only because companies do not track the devices well.
SISA’s Approach: Assurance and operations members of risk and compliance teams must update the device lists with changing employees. The best solution to tackle this PCI DSS control is to maintain an accurate inventory with proper labelling and set a shorter frequency for updating the list with 4 columns – device, employee, data type, and access type.
Requirement 12.10.1.a: Verify incident response plan
Off-the-shelf security incident response plans remain outdated and ineffective against the ever-changing threat landscape. For compliance analysts and managers, verification of plans only goes so far. Each year, SISA performs hundreds of incident response exercises across the globe. During these engagements, we have observed incident response plan failures mostly because of organizational shortcomings that form a major part of the PCI DSS requirements. Failing to plan means planning to fail.
SISA’s Approach: Businesses opting to verify their incident response plans for PCI DSS compliance must simulate a real-world attack every 6 months and assess how key stakeholders respond to it. Operational security teams must, in such events, document issues and lessons against specific scenarios of PCI DSS incident response requirements including organizational coordination, business recovery, data backup, and analysis of legal requirements.
Note: In the case of a suspected or confirmed security breach, payments merchants and service providers must act within 24 hours to alert all necessary parties including internal information security teams and merchant banks(s).
Requirement 12.5.5: Monitor and control all access to data
All data custodians and key management professionals that give access to data based on a business’ need to know must be solely responsible to monitor the access hygiene. However, businesses ignore the importance of bestowing this responsibility to an individual with formal accountabilities. This has become crucial ever since remote working has increased as companies aren’t able to ensure that the type of access given is appropriate and all technical safeguards are in place for data access.
SISA’s Approach: A data security specialist with a straight-line reporting to the executive authority of the firm (CIOs, CISOs, Information Security Managers, Chief Data Officers, Risk and Compliance Managers, etc.) must be nominated for such responsibilities. QSAs at SISA recommend such professionals to implement privileged access management and update the data access charts on a monthly basis.
Embracing a culture of compliance
Although the regulatory landscape for PCI SSC compliance requirements continues to evolve, the foundation of expectations set from a PCI DSS compliance program remain – to encourage businesses to secure cardholder data and embrace a culture of compliance with consistent data security measures. Therefore, risk and compliance teams can remain focused on how to further enhance their compliance controls. They can do so by looking at the most critical requirements that they may fail to achieve. For PCI DSS compliance, the best starting point for businesses are the 5 controls mentioned in this blog post.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  X
X Youtube
Youtube








