Nefilim Ransomware

Countless news reports have documented the outbreak of Nefilim ransomware and many organizations across a range of industries have been affected by the ransomware’s attacks. In this article we have summarized the root causes of Nefilim ransomware and ways to prevent it.
A Covid-19 vaccine trial was bogged down in recent weeks when researchers were locked out of their data as the result of a ransomware attack. This is a small instance of the toll from ransomware attacks; city governments have been crippled, hospitals have been forced to turn away emergencies, and small businesses have been shuttered.
Surfaced and began spreading at the end of February 2020
Since then, Nefilim (also called Nephilim) ransomware has encrypted files with AES-128 encryption, protected by RSA2048, and infected them by appending “.NEFILIM” in innumerable cases. The signatures on the code resemble those of Nemty ransomware family and instead of using a Tor payment site, the malicious software relies on email communication with victims for payment. Here are a few cases of how the Nefilim ransomware has disturbed normal business.
- May 2020: An Australian transportation company has lost over 200GB of corporate data and its customers have experienced significant delays as a result of the Nefilim ransomware attack.
- June 2020: A New Zealand based white-goods manufacturer was targeted by the Nefilim ransomware and its corporate files were exposed on the dark web.
- July 2020: A German facilities management multinational’s 16,000 sensitive business files were leaked to the dark web by the Nefilim ransomware attackers and the servers were temporarily shut down as a result of the mishap.
- September 2020: Italy-based eyewear and eyecare giant shut down operations in Italy and China when attacked by the Nefilim ransomware.
- December 2020: Home appliances giant’s data was leaked that included documents related to employee benefits, accommodation requests, medical information requests, background checks, and more.
- Year 2021: New Nefilim ransomware variants have been discovered that append the “.DERZKO” and “.MILIHPEN” to drop ransom notes named “DERZKO-HELP.txt” and “MILIHPEN-INSTRUCT.txt” respectively.
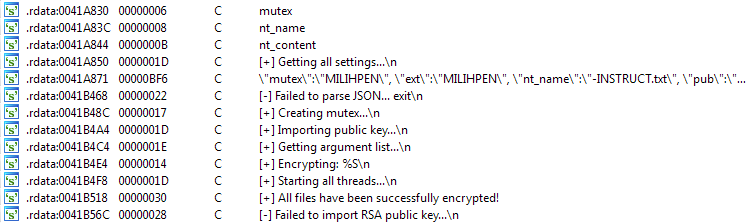
Source: Twitter/MalwareHunterTeam
Initial Access of Nefilim Ransomware
The Nefilim ransomware exploits public-facing applications for initial access. The operators of Nefilim ransomware target organizations with unpatched or poorly secured Citrix remote access technology, threatening to release its victims’ data to the public if they fail to pay the ransom. It is most likely distributed through exposed Remote Desktop Protocol (RDP). Nefilim’s code shares many notable similarities with Nemty 2.5 ransomware; the main difference is the fact that Nefilim has done away with the Ransomware-as-a-Service (RaaS) component. It also manages payments via email communications rather than through a Tor payment site.
Nefilim spreads itself in two ways:
1. NEFILIM is a newly emerged ransomware and is most likely distributed through exposed Remote Desktop Protocol (RDP).
2. It uses several other ways to penetrate into IT systems, including:
- Spam emails
- P2P file sharing
- Free software
- Malicious websites
- Torrent websites
Execution of Nefilim Ransomware
Nefilim directly interacts with the native OS API to execute behaviors. For instance, after compromising the RDP, an attempt is made to download a malicious file that in return downloads a RAR archive from a VPS-hosted server. A few hours later, it makes an attempt to download a RAR archive containing multiple files, the details of which are described below:
- The ransomware file itself
- Psexec.exe, to executes remote commands
- A batch file to stop services/kill processes
- A batch file that uses ‘copy’ command to distribute the batch file that stops services/kills processes to multiple hosts, on c:\Windows\Temp
- A batch file that uses ‘copy’ command to spread the ransomware file to multiple hosts, on c:\Windows\Temp
- A batch file that utilizes WMI to distribute the batch file that stop services/kill processes to multiple hosts, on c:\Windows\Temp. Contains hard-coded admin credentials.
- A batch file that utilizes WMI to distribute the ransomware file to multiple hosts, on c:\Windows\Temp. Contains hard-coded admin credentials.
- A batch file that executes psexec.exe to remotely execute the batch file to stop services/kill processes. Contains hard-coded admin credentials.
- A batch file that executes psexec.exe to execute the ransomware file remotely. Contains hard-coded admin credentials.
- A batch file that utilizes WMI to remotely execute the batch file to stop services/kill processes. Contains hard-coded admin credentials.
- A batch file that utilizes WMI to execute the ransomware remotely. Contains hard-coded admin credentials.
After downloading the RAR archive, a combination of the batch files mentioned above is used in tandem to ensure success:
- A combination of the batch files is used to make sure that the distribution of the batch file that stops services/kills processes including the ransomware was done via copy command or WMI
- Remote execution is made possible through stolen admin credentials via PSexec or WMI
Encryption by Nefilim Ransomware
- Once the operators launch the attack, the Nefilim ransomware uses a combination of AES-128 and RSA-2048 algorithms to encrypt the victims’ files. First, the files are encrypted using AES-128 encryption and AES encryption key is further encrypted using the RSA-2048 public key. This key is then embedded in the executable file of the ransomware.
- The file extension name. NEFILIM is appended at the end of each encrypted file name along with a NEFILIM file marker for all encrypted files. This is how the ransomware gets its name.
- On successfully encrypting all files, the ransomware plants a ransom note ‘NEFILIM-DECRYPT.txt’ that instructs the victim on how to recover their files. New variants of the append and ransom note have been found recently.
- The ransom note contains different contact emails for contacting its operators. It also includes a line that warns victims of leaking their data if the ransom is not paid within seven days.
Nefilim Ransom Notes
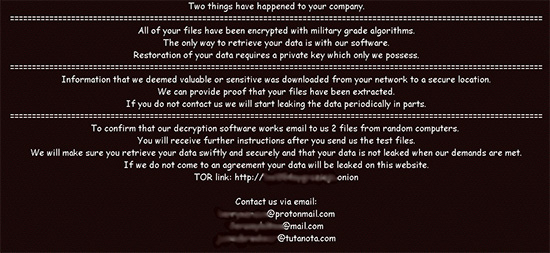
Source: SentinelLABS
Nefilim TTP Map
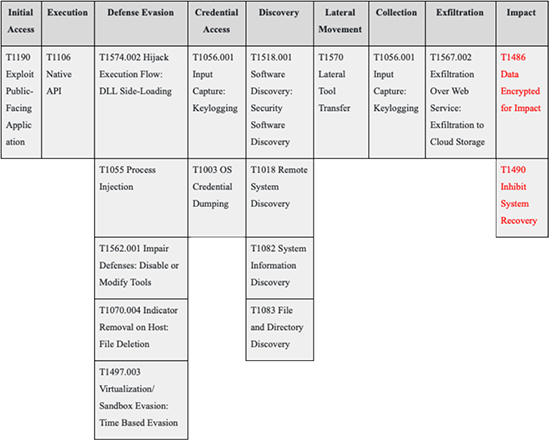
Source: Picus Security
INDICATORS OF COMPROMISE – Nefilim Ransomware
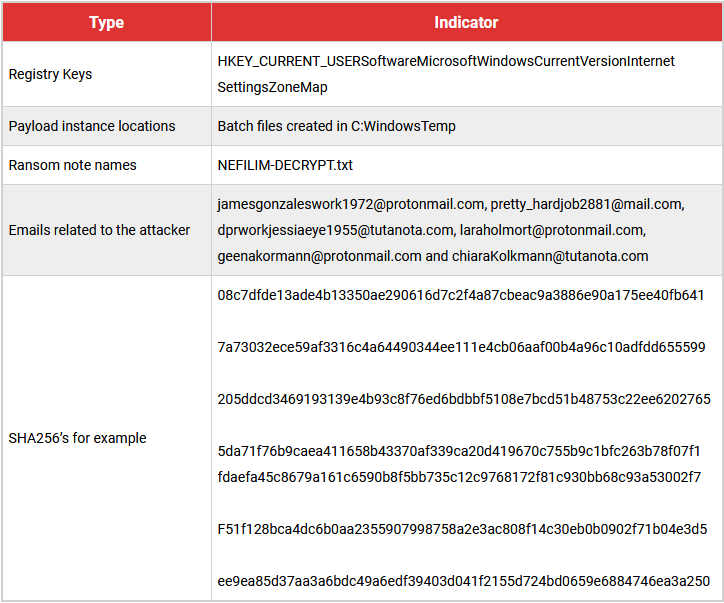
Nefilim Ransomware Mitigation
- Make sure your RDP connection is not open to the internet. If not using RDP, close TCP Port 3389 on the computers. Enable network level authentication for RDP.
- Block the IoCs in the corresponding security devices.
- In order to protect the systems from ransomware in general, it is important that users use good computing habits and security software. First and foremost, always have a reliable and tested backup of the data that can be restored in the case of an emergency.
- Make sure that all systems and software are updated with relevant security patches.
- Do not open emails and mail attachments from unknown people.
- Do not download or use software cracks and illegal software.
Ransomware attacks have become pervasive enough – and the ransom payments regular enough – that businesses are getting vulnerable when it comes to dealing with attackers that wipe sensitive files locked down during a ransomware attack. There are no great choices, but businesses can always take preventive steps, strengthen cyber defense, and become resilient.
References:
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/investigation-into-a-nefilim-attack-shows-signs-of-lateral-movement-possible-data-exfiltration
- https://www.bleepingcomputer.com/news/security/home-appliance-giant-whirlpool-hit-in-nefilim-ransomware-attack/
- https://www.techcert.lk/en/alerts-news/297-nefilim-ransomware
- https://www.picussecurity.com/resource/blog/how-to-beat-nefilim-ransomware-attacks
- https://www.bleepingcomputer.com/news/security/orange-confirms-ransomware-attack-exposing-business-customers-data/
- https://kc.mcafee.com/corporate/index?page=content&id=KB93623&locale=en_US
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global

 Facebook
Facebook Linkedin
Linkedin  Twitter
Twitter Youtube
Youtube








