Indicators of Behavior: A Shift to Cyber Resilience

Cybersecurity teams assume that once there is a match between an Indicator of Compromise (IoC) and the generated logs, they will be able to successfully detect a potential threat. Wrong.
Businesses have arguably seen more advanced cyberattacks in the last 12 months than in the last 12 years, bringing new and urgent task for cybersecurity teams to advance their threat hunting capabilities. For information security teams across the globe, this metaphor has come to embody the threat hunting challenge they want to counter: “efficient use of IoCs for detecting incidents.”
What’s better than the use of IoCs, anyway? IoBs. Indicators of Behavior is the behavioral telemetry and analytics methodology that adds context to threats in real-time. One might wonder, considering the nature of IoBs focused on the behavior of attackers, how is there a chance for cybersecurity teams to leverage IoBs to counter supply-chain attacks. This article is all about IoBs and the extent to which they can be a great way to hunt down threats in real-time.
NOTE: We are not recommending making a choice between IoCs or IoBs for detection and response purposes. This article discusses major distinctions between IoCs and IoBs, and new approaches of how IoBs can act as a supplement for existing MDR solutions to transform from a reactive to preventive mode. While many restrict the use of IoBs to the detection of insider threats, this article opens the doors of possibilities in using IoBs for hunting advanced threats and attacks. Ultimately, this article reflects on notable ways of adopting advanced technologies such as AI to build cyber resilience.
Indicators of Behavior vs. Indicators of Compromise
While IoCs are pre-recorded, static artifacts that signal threats on a network through a mix and match approach, IoBs are the behavioral particulates of different components of the complete infrastructure that determine the context and intent of a threat.
IoCs are identified in the form of IP addresses, domain names of botnet command and control servers, and file hashes, or other properties of an environment that describe the risk factor involved. MITRE’s Structured Threat Information eXpression project, STIX™, sponsored by the Department of Homeland Security, specifies common attack patterns and Indicators of Compromise that serve as a useful tool for many businesses to detect threats.
On the other hand, IoBs are dynamic digital impressions and identifiers that monitor the interaction of foreign bodies with host systems or networks. From a threat detection and awareness perspective, IoBs help add context to the detections. To understand it better, ask yourself the following questions: Which stage of the attack have we detected? Has the attacker already established foothold? IoBs help you with answers to these questions. They also help you understand the behavior of potential cyberattackers.
Differences between working models of IoCs and IoBs
| IoCs | IoBs |
| Anomalies in Privileged User Account Activity | Unusual Updates in Vendor Software |
| Large Numbers of Requests for the Same File | Interactions with Unchecked Code Repositories |
| Mismatched Port-Application Traffic | Increment of Users on Emulated or Virtualized Systems |
| Unusual Outbound Network Traffic | Internal-External Host Communication Distracted |
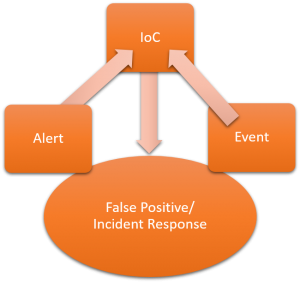 |  |
In a hypothetical situation, entry point of a malware can be frequently changed by attackers for de-obfuscated malicious executable. In such cases with iterated obfuscation, IoCs alone won’t be effective for threat intelligence. Moreover, the use of IoCs have been a pose of challenge for cybersecurity teams due to the high rate of false positives and outdated indicators.
Tools and skills required for using Indicators of Behavior in threat hunting process
IoBs emphasize on the left side of a cyber kill chain. So, how far companies are ready to stretch their knowledge base very much will illustrate their readiness to adopt the IoB approach for threat hunting. Sophisticated adversaries are trying to mutate almost every recon strategy of the past. So, the next attack might not be one from the holy book of IoCs.
Unlike rule-based models, Indicators of Behavior take on a new approach of studying dynamic heuristics that takes into account all the interaction or information effects of foreign bodies with host networks. Therefore, in practice, IoBs can be a part of the telemetry unit that forms a major part of the threat intelligence, and detection and response services. While it may require a greater level of effort to elevate the coverage of behaviors that can possibly be a pose of threat, a machine learning model with the right datasets may prove far effective.
Tools, techniques and software used for detecting threats can be introduced with a catalogue of behaviors that respond to K-nearest neighbor (KNN) classification algorithm for multidimensional attack vectors. Ultimately, IoBs would be assumptions, attitudes, perceptions, values, and knowledge from forensic investigations that indicate potential threats in a network.
SISA Dhi The award-winning reverse engineered forensics threat hunting process automated using inhouse developed machine learning Algorithm, SISA Dhi can help you find the true positives with assisted human intelligence. |
Benefits of using IoBs for threat hunting
In most cases, the inclusion of IoBs in threat hunting has proven to reduce the number of false positives dramatically. However, following are a few advantages of leveraging IoBs along with other threat intelligence channels such as CVEs, IoCs, or risk scores.
| Move Left of Breach | Prioritize Risk |
|
|
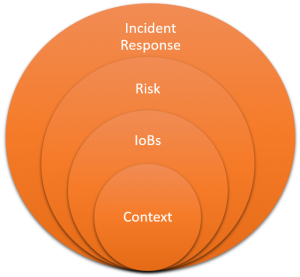
Scope and applicability of Indicators of Behavior for threat hunting
Indicators of Behavior is not based on the interpretation of empirical data. Therefore, it is easy for analysts to derive practical scenarios of using IoBs for threat hunting.
Following are a few use cases of the same:
- Insider Threats Identification
- Compromised Device Detection
- Data Leakage Prevention
- Incident Prioritization
- Endpoint Risk & Health
- Entity Analytics – IoT
Using Indicators of Behavior as a starting point to identify threats is a hard job. Yet an ignition of the concept, with the pervasive threat intelligence tools, is crucial for fighting tomorrow’s advanced cyberattacks. Only a few businesses aware of their cybersecurity posture are making an attempt to adopt next-gen technologies for cybersecurity. Those businesses have, knowingly or unknowingly, leveraged IoBs as a key tool to build cyber resilience.
 USA
USA India
India APAC
APAC Middle East
Middle East Global
Global




 Facebook
Facebook Linkedin
Linkedin  Twitter
Twitter Youtube
Youtube








